Cybersecurity researchers have disclosed a number of safety flaws in video surveillance merchandise from Axis Communications, which, if efficiently exploited, can now take over the assault.
“This assault may have pre-certified distant code execution in Axis Machine Supervisor, servers used to configure and handle digicam fleets, and Axis digicam stations for consumer software program used to view digicam feeds.”
“As well as, utilizing Web scanning of uncovered axes, attackers can enumerate susceptible servers and purchasers and perform granular, extremely focused assaults.”
The record of recognized defects is as follows:
- CVE-2025-30023 (CVSS rating: 9.0) – Flaws within the communication protocol used between purchasers and servers can result in authenticated customers performing distant code execution assaults (mounted with Digital camera Station Professional 6.9, Digital camera Station 5.58, and Machine Supervisor 5.32)
- CVE-2025-30024 (CVSS rating: 6.8) – A defect within the communication protocol used between consumer and server. This may be utilized to hold out intermediate (AITM) assaults (mounted with Machine Supervisor 5.32)
- CVE-2025-30025 (CVSS rating: 4.8) – Flaws in communication protocol used between server processes and repair controls that may result in native privilege escalation (mounted with Digital camera Station Professional 6.8 and Machine Supervisor 5.32)
- CVE-2025-30026 (CVSS rating: 5.3) – Axis digicam station server defects that might result in authentication bypass (mounted with Digital camera Station Professional 6.9 and Digital camera Station 5.58)

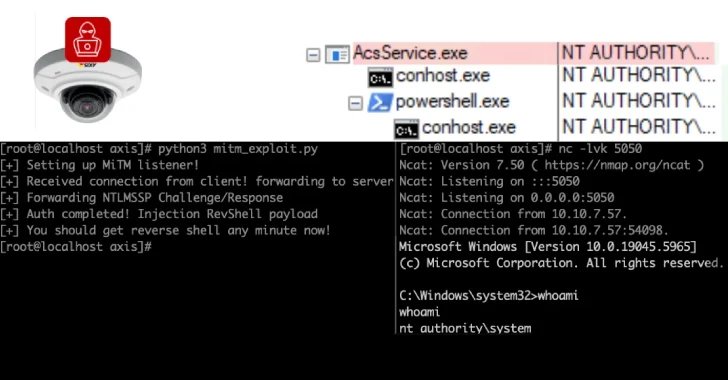
The profitable exploitation of the aforementioned vulnerability permits an attacker to imagine the AITM location between the digicam station and its purchasers, successfully modifying requests/responses and performing any motion on both the server or consumer system. There isn’t a proof that the issue was exploited within the wild.
Claroty stated it discovered over 6,500 servers that expose their very own axis.
“A profitable exploit provides the attacker system-level entry on the interior community and the flexibility to manage every digicam in a specific deployment,” Moshe stated. “The feed could be hijacked, monitored, and/or shut down. Attackers can benefit from these safety points to bypass authentication to the digicam and procure distant code execution earlier than authentication on the gadget.”