Safety researchers have launched a partial proof of idea for a vulnerability within the FortiWeb Net Utility Firewall that permits distant attackers to bypass authentication.
The defect was reported responsibly to Fortinet and is presently being tracked as CVE-2025-52970. Fortinet launched the repair on August twelfth.
Safety researcher Aviv Y has named the vulnerability Fortmajeure, describing it as “a silent failure that was not supposed to happen.” Technically, permitting an attacker to set the ERA parameter to an sudden worth is a missed learn in Fortiweb’s Cookie Parsing.
This makes the server trivial to create a solid authentication cookie, utilizing a full-zero secret key for session encryption and HMAC signature.
Exploitation causes a whole authentication bypass, inflicting attackers to impersonate lively customers, together with directors.
To make good use of CVE-2025-52970, the goal person should have lively periods in the course of the assault, and the enemy should brute drive a small numeric discipline to the cookie.
The brute enhancement necessities come from the fields of the signed cookies validated by the operate REFRESH_TOTAL_LOGINS() (libncfg.so).
This discipline is an unknown quantity that an attacker should guess, however researchers often level out that the vary just isn’t exceeding 30, making it a small search house for round 30 requests.
Exploit makes use of the All-Zero key (resulting from an ERA bug), so you may check every guess instantly by checking whether or not a solid cookie is accepted.
This situation affected FortiWeb 7.0 to 7.6 and was mounted within the following variations:
- Fortiweb 7.6.4 or later
- Fortiweb 7.4.8 or later
- Fortiweb 7.2.11 or later
- Fortiweb 7.0.11 or later
Fortinet mentioned within the breaking information that the discharge of Fortiweb 8.0 is not going to be affected by this situation, so there isn’t any motion to take there.
Because the safety bulletin doesn’t checklist workarounds or mitigation recommendation, upgrading to a protected model is the one beneficial and efficient motion.
Fortinet’s CVSS severity rating could also be misleading of seven.7. It’s because it comes from the “excessive assault complexity” because of the brute-enhancing necessities. However in actuality, the half that reinforces the brute is straightforward and fast.
Researchers shared the POC output and confirmed administrator spoofing on the REST endpoint. Nevertheless, he withdrew the total exploit overlaying connecting to the Fortiweb CLI by way of /ws/cli/open.
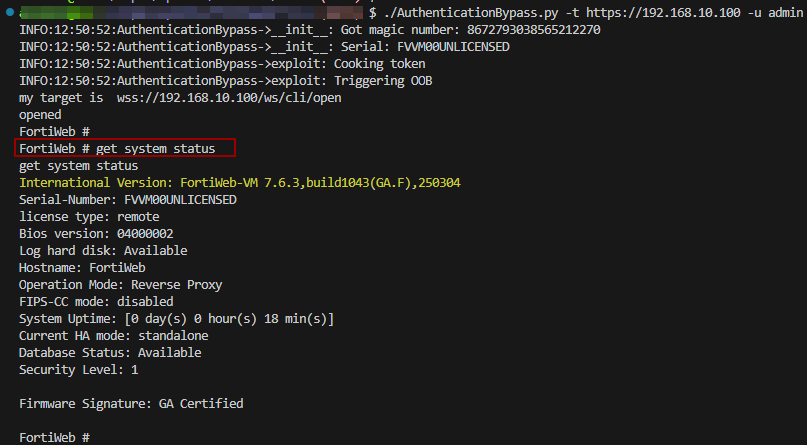
Supply: Aviv Y
Nevertheless, Aviv Y has pledged to launch the small print of the whole exploitation later, as the seller’s advisory was not too long ago launched. Researchers made this resolution to extend the time that system directors ought to apply corrections.
The printed particulars present the core of the issue, however even educated attackers are usually not sufficient to invest on the remainder and develop a totally weaponized chain, researchers advised BleepingComputer.
He defined that the attacker must reverse engineer the format of the session’s discipline. That is unrealistic on condition that Fortinet has its personal information construction.
However, hackers have adopted these bulletins intently and must take speedy steps to mitigate the difficulty as they put together to drag the set off when the total POC comes out.
Aviv Y advised BleepingComputer that it has not selected a date to publish the exploit, however plans to provide defenders time to answer the danger.









