Cybersecurity researchers have introduced new findings associated to safety points associated to communication protocols that may be abused by attackers and misused by attackers by recognized servers.
The vulnerability tracked as CVE-2025-49760 (CVSS rating: 3.5) has been described by the Tech big as a spoofing bug in Home windows storage. Corrected in July 2025 as a part of the month-to-month patch Tuesday replace. Particulars of the safety flaw have been shared by Safebreach researcher Ron Ben Yizhak at this week’s DEF Con 33 safety convention.
“Exterior management of Home windows storage filenames or paths permits licensed attackers to carry out spoofing on the community,” the corporate mentioned in an advisory launched final month.
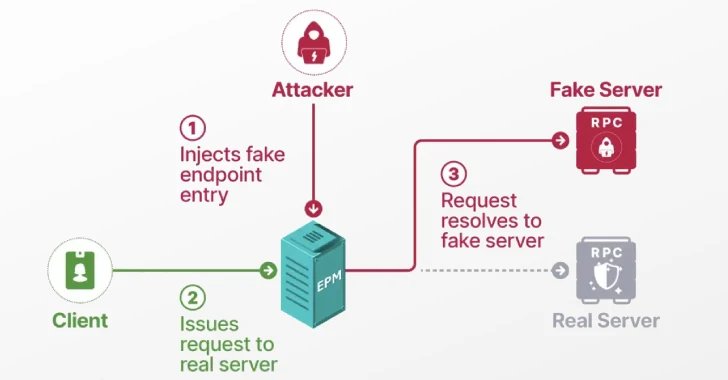
The Home windows RPC protocol makes use of a universally distinctive identifier (UUID) and endpoint mapper (EPM) to attach an RPC consumer to the server-registered endpoint to allow the usage of dynamic endpoints in client-server communications.
The vulnerability primarily permits it to be set in what known as EPM habit assaults, which permit unprivileged customers to pose as a authorized, built-in service, with the intention of sustaining a protected course of to govern core elements of the RPC protocol and authenticate in opposition to any server of the attacker’s alternative.
Provided that the performance of EPM is just like that of the Area Identify System (DNS), it maps the interface uuid to the endpoint. Solely DNS resolves a site to an IP tackle. Assaults play like DNS habit.
- Poison EPM
- Masked Stage as a reputable RPC server
- Function the RPC consumer
- Obtain native/area privilege escalation by way of ESC8 assaults
“We have been shocked that nothing was stopping us from registering recognized built-in interfaces belonging to the Core Providers,” Ben Ijak mentioned in a report she shared with Hacker Information. “For instance, if a Home windows Defender had a novel identifier, we anticipated that different processes wouldn’t be capable to register, however that wasn’t the case.”
“After I tried to register an interface for a service that was turned off, the consumer related to me as an alternative. This discovery was unbelievable. There have been no safety checks accomplished by EPM.
The guts of an assault depends on discovering interfaces that aren’t mapped to the endpoint. Additionally, many providers are set to “delayed begin” for efficiency causes, permitting them to register instantly after the system boot by making the boot course of sooner.
In different phrases, providers with handbook startup are a safety danger, as RPC interfaces usually are not registered for boot. By permitting attackers to register the interface earlier than the unique service, it’s successfully prone to hijacking.

SafeBreach flags unstable RPC providers (similar to storage providers and StorSVC.DLL), releases a software known as RPC-Racer that can be utilized to function protected course of lights (PPLs), permitting machine accounts to the servers chosen by the attacker.
PPL expertise ensures that the working system solely masses dependable providers and processes, defending the operating course of from termination or an infection by malicious code. It was launched by Microsoft within the launch of Home windows 8.1.
At a excessive stage, the whole assault sequence is as follows:
- Creates a scheduled job that can run when the present consumer is logged in
- Register the storage service interface
- Triggering a supply optimization service to ship RPC requests to the storage service and connect with the attacker’s dynamic endpoint
- Name the tactic getStorageEviceInfo().
- Supply Optimization Providers authenticate with malicious SMB server utilizing machine account credentials and leak NTLM hash
- Stage ESC8 assaults to relay compelled NTLM hash to a web-based certificates enrollment service (AD CS) to attain privilege escalation
To realize this, you need to use an offensive open supply software like Certipy to request a Kerberos Ticket Cultivation Ticket (TGT) utilizing a certificates generated by passing NTLM data to an AD CS server, and use it to dump all of the secrets and techniques from the area controller.
Safebreach mentioned it may additional prolong its EPM habit expertise to hold out interim (AITM) and denial of service (DOS) assaults by forwarding requests to the unique service or registering many interfaces every to disclaim the request. The cybersecurity firm additionally famous that there might be different purchasers and interfaces which can be susceptible to EPM habit.
To higher detect a lot of these assaults, safety merchandise can use occasion tracing in Home windows (ETW), a safety characteristic that displays calls to RPCEPregister and information occasions raised by user-mode purposes and kernel-mode drivers.
“It’s essential confirm the id of your RPC server in order that SSL pinning ensures that the certificates isn’t solely legitimate, however that it makes use of a selected public key,” says Ben Yizhak.
“The present design of the Endpoint Mapper (EPM) doesn’t carry out this validation. With out this validation, the consumer accepts information from unknown sources. By blindly trusting this information, the attacker can management the consumer’s actions and manipulate the attacker’s will.”