The large spike within the brute power assault focused Fortinet SSL VPN earlier this month, concentrating on the change to Fortimanger, indicating a deliberate change in concentrating on that had traditionally preceded disclosure of recent vulnerabilities.
The marketing campaign was detected by menace surveillance platform Greynoise and seems in two waves on August 3 and August 5, with the second wave concentrating on the goal with a special TCP signature.
As beforehand reported by Greynoise, such spikes in intentional scans and brute-fasting are 80% of the time previous to disclosure of recent safety vulnerabilities.
In lots of circumstances, such scans goal to enumerate uncovered endpoints, assess their significance and estimate their potential for exploitation.
“New analysis reveals that these spikes usually precede disclosures of recent vulnerabilities affecting the identical vendor.
“Actually, Greynoise has found that the spikes on this actual tag-triggering exercise are considerably correlated with apparent future vulnerabilities in Fortinet merchandise.”
Subsequently, advocates mustn’t dismiss these spikes of their actions to deal with them as potential precursors of zero-day disclosures, as makes an attempt to use outdated, patched flaws have failed, and to boost safety measures that block them.
Fortinet Brute-Pressure Assault
On August 3, 2025, Greynoise recorded a spike in a brute-fasting try concentrating on Fortinet SSL VPN as a part of a secure exercise that has been monitored for a very long time.
JA4+ Fingerprint Evaluation, a community fingerprinting technique for figuring out and classifying encrypted visitors, linked the spike to a June exercise derived from the Fortigate machine with a residential IP handle related to pilot Fiber Inc.
“This overlap doesn’t verify attribution, however suggests the potential of reuse of the device or community atmosphere,” Greynoise commented within the breaking information.
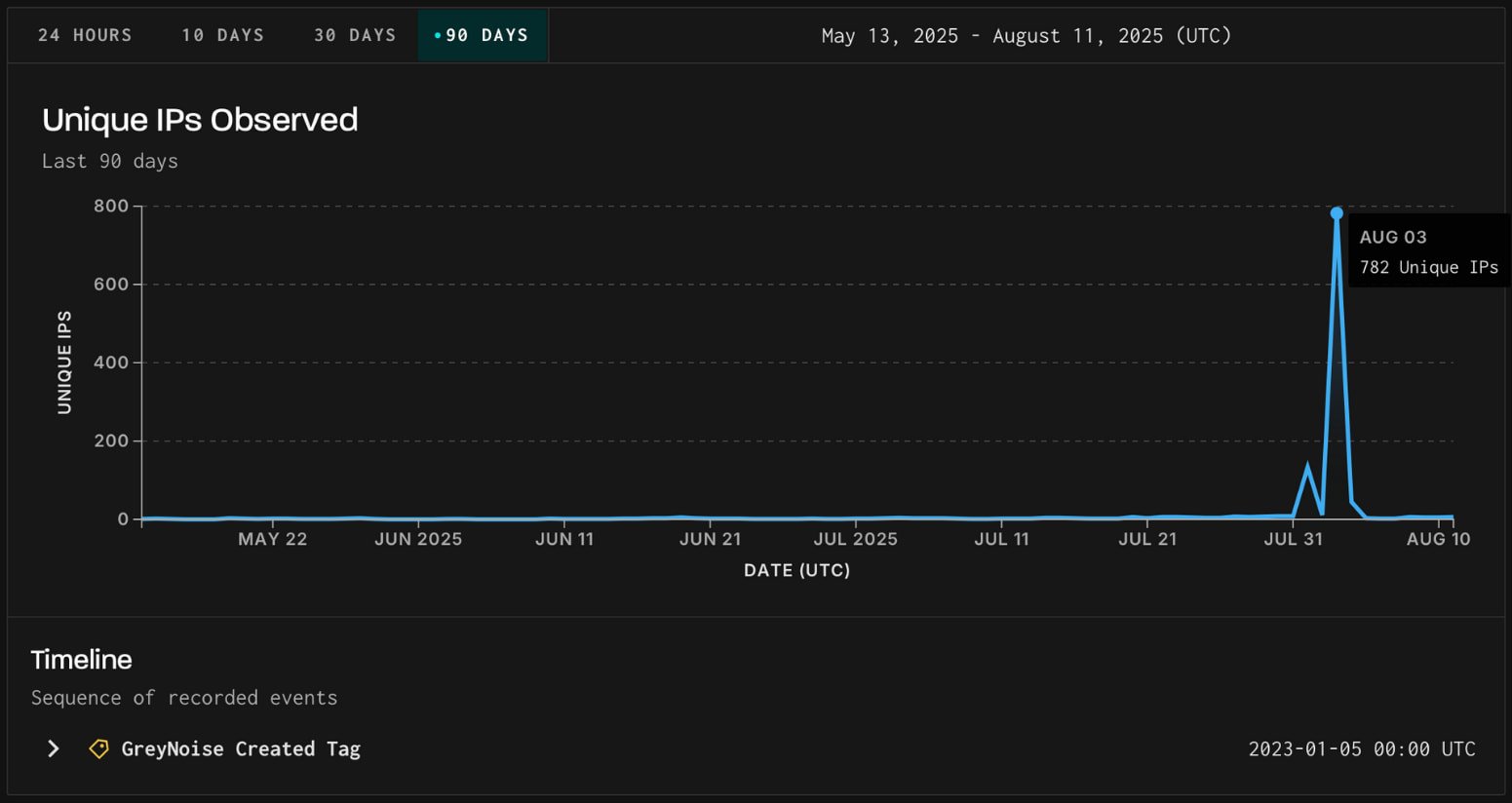
Supply: Greynoise
Two days later, on August fifth, a brand new brute power marketing campaign from the identical attacker appeared, switching concentrating on from the Fortios SSL VPN endpoint to Fortimager’s FGFM service.
“Site visitors on August third is focused. Fortius No fingerprinted visitors with TCP and shopper signatures (meta signatures) has been hit since August fifth Fortius“Gray Noise defined.
“As a substitute, it was constantly concentrating on us. Fortimagar -FGFM Though the profile nonetheless triggers the Fortinet SSL vpn bruteforcer tag. ”
This shift means that both the identical attacker or the identical toolset/infrastructure will transfer to Brute-Pressure Fortimager Entry as they try to attempt a VPN login.
The IP addresses related to this exercise, and these addresses, have to be positioned within the block record.
- 31.206.51.194
- 23.120.100.230
- 96.67.212.83
- 104.129.137.162
- 118.97.151.34
- 180.254.147.16
- 20.207.197.237
- 180.254.155.227
- 185.77.225.174
- 45.227.254.113
Greynoise factors out that tracked malicious actions have advanced over time and are associated to particular origin clusters which can be almost certainly to carry out adaptive checks.
Typically, this exercise shouldn’t be a researcher scan. Researcher scans are often broad vary, restricted charges, and don’t contain brute power of {qualifications} which can be thought-about an apparent intrusion try.
Subsequently, defenders ought to block listed IPS, enhance login safety for Fortinet gadgets, improve exterior entry when doable, and restrict entry to solely trusted IP ranges and VPNs.