Risk actors use Unicode characters to make phishing hyperlinks appear like legit Reserving.com hyperlinks for brand new campaigns delivering malware.
This assault makes use of a Japanese Hiragana character. This seems in some programs as a ahead slash, making the phishing URL look real looking at an informal, look.
BleepingComputer has come throughout extra within the Intuit Phishing marketing campaign utilizing the Lookalike Area, utilizing the letter L as a substitute of Intuit’s “I”.
Reserving.com Fishing Hyperlink makes use of Japanese homoglyphs
The assault first found by safety researcher James abuses the Japanese Hiragana character “N” (Unicode U+3093), which is similar to the Latin character sequence “/n” or “/~” at a look in a number of fonts. This visible similarity permits scammers to create URLs that seem to belong to the true Reserving.com area, however customers will direct them to malicious websites.
Under is a duplicate of a phishing e-mail shared by safety researchers.
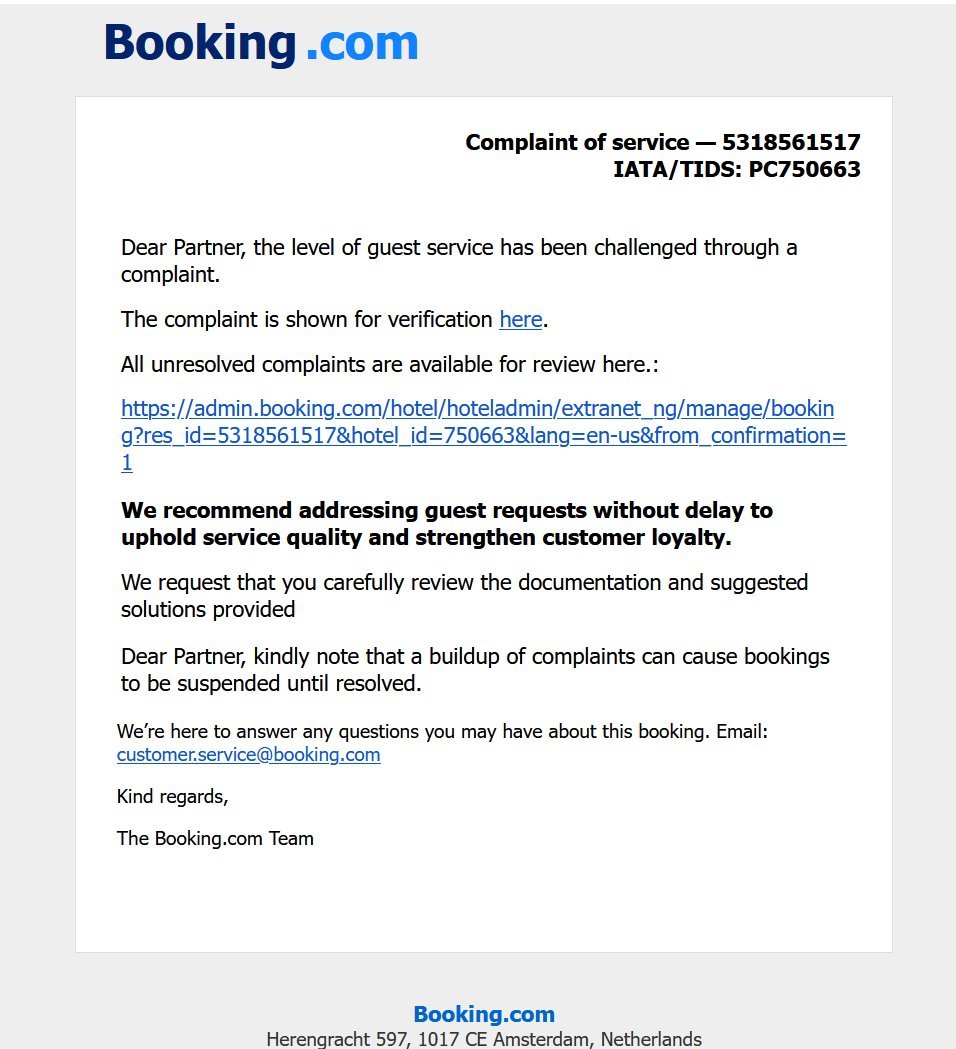
E-mail textual content, https://admin.reserving.com/resort/hoteladmin/… That in itself is misleading. It might appear like a Reserving.com tackle, however the hyperlink is:
https://account.reserving.comんdetailんrestric-access.www-account-booking.com/en/
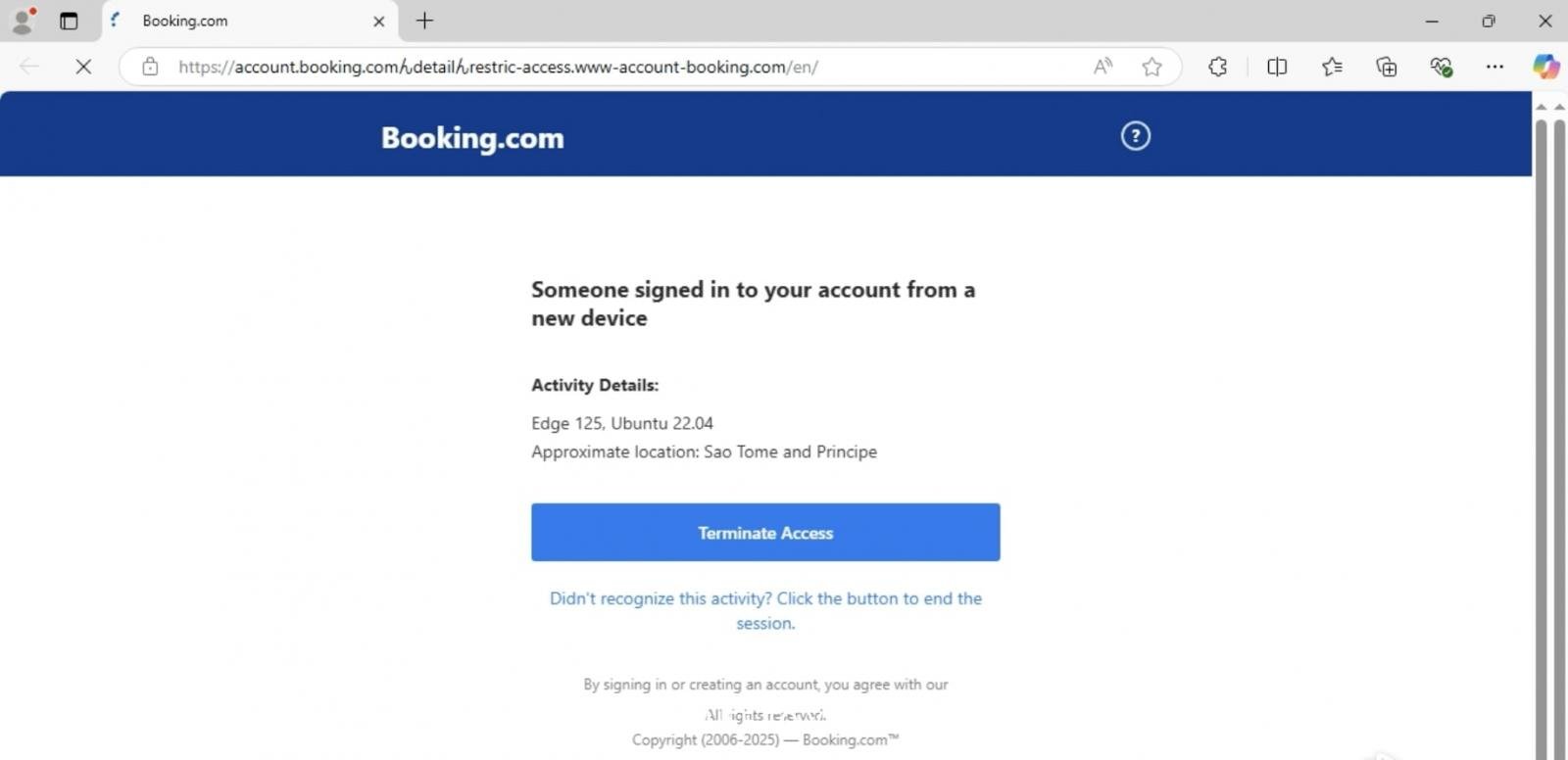
When rendered within the tackle bar of an internet browser, the “hmm” character is tricking the person into navigating a subdirectory of Reserving.com.
In reality, the precise registered area is www-account-booking(.)commalicious look, and earlier than that, all the pieces is a misleading subdomain string.
The victims of click-through are in the end redirected as follows:
www-account-booking(.)com/c.php?a=0
This may present a malicious MSI installer from the CDN hyperlink. https://updatessoftware.b-cdn (.)internet/john/pr/04.08/iytdtgtf.msi
Pattern malicious websites can be found on MalwareBazaar on Aubse.ch. MSI information are probably used to drop further payloads, together with Infostealers or Distant Entry Trojans.
This phishing tactic exploits uniform ones. A homoglyph is a personality that resembles one other character, however belongs to a special character set or alphabet. These visually related characters could be exploited in phishing assaults or create deceptive content material. For instance, the Cyrillic letter “о” (u+041e) could look the identical because the human and the Latin letter “o” (u+004f), however they’re completely different letters.
Given the visible similarity, homographs have been used many times by risk actors in homograph assaults and phishing emails. Moreover, defenders and software program builders have deployed safety measures over the previous few years that permit customers to simply distinguish between clear homoglyphs.
This isn’t the primary time a risk actor has focused Reserving.com clients.
In March this yr, Microsoft warned in its phishing marketing campaign that it could use a ClickFix social engineering assault to contaminate hospitality employees with malware.
In 2023, Akamai revealed that hackers have been redirecting resort visitors to faux Reserving.com websites to steal bank card data.
“lntuit” is just not instinct
Sergiu Gatlan from BleepingComputer has found one other phishing marketing campaign that features customers focused by Intuit-themed emails.
These emails appear to come back from you and take you Intuit.com Addresses use the primary area as a substitute lntuit –Lowercase letters can resemble the “instinct” of a selected font. Easy but efficient method.
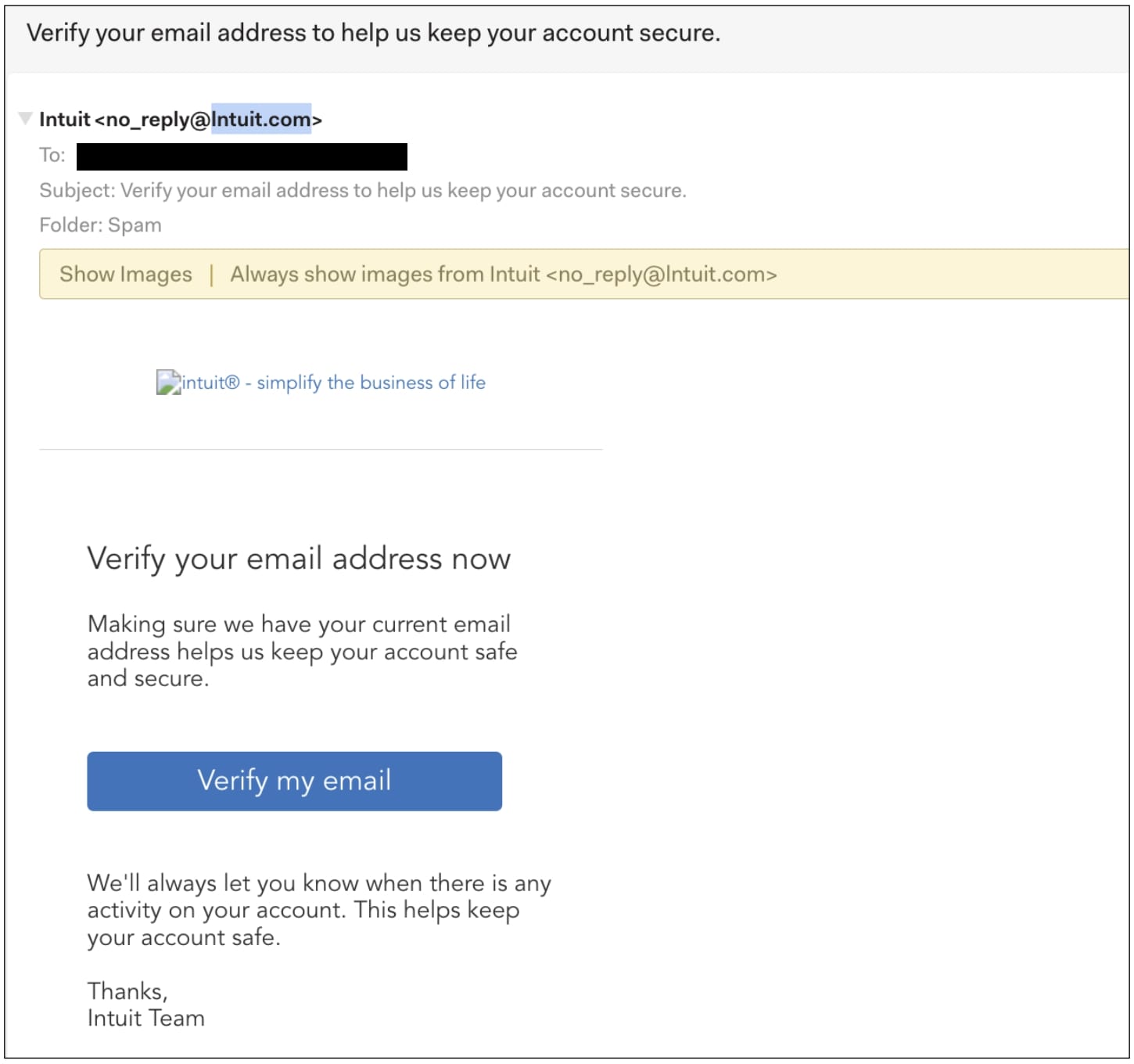
This unusually slim structure of emails on desktop shoppers means that they’re primarily designed for cell viewing, suggesting that cell person attackers are clicking on the “verify e-mail” phishing hyperlink with out scrutiny.
The button appears like this: https://intfdsl(.)us/sa5h17/
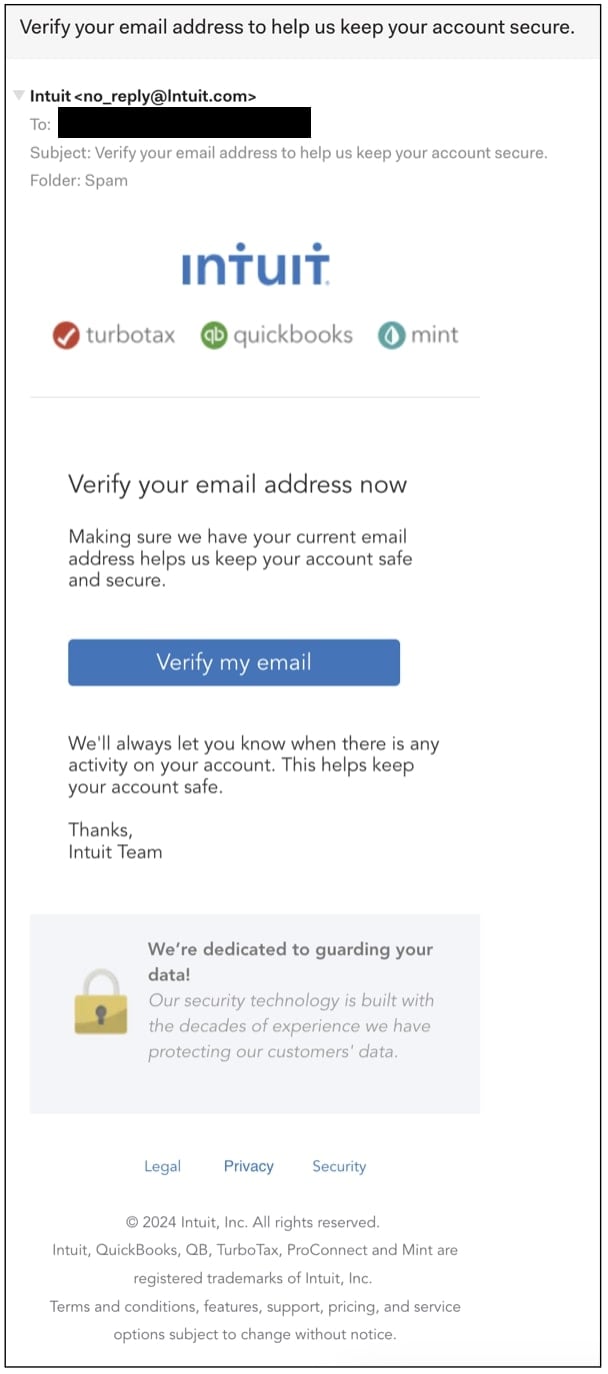
Apparently, unlawful hyperlinks seem to redirect customers to legit Intuit.com login web page when accessed straight from the goal person’s e-mail account. https://accounts.intuit.com/app/sign-in.
These incidents remind us that attackers proceed to search out inventive methods to abuse typography for social engineering.
To guard your self, at all times hover over the hyperlink earlier than clicking to view the true goal.
The person ought to at all times verify the precise area on the far proper of the tackle earlier than the primary single /- That is the precise registered area. Definitely, utilizing visually misleading Unicode characters like “hmm” creates further hurdles, indicating that visible URL inspection alone is just not totally full.
Retaining your endpoint safety software program up-to-date provides one other layer of protection towards assaults, as the most recent phishing kits usually ship malware straight after a phishing hyperlink is clicked.









