The mixture of propagation strategies, narrative refinement, and evasion strategies has enabled social engineering ways generally known as Clickfix A brand new survey from Guardio Labs exhibits that they are off the way in which they did the previous yr.
“This new factor, like a real-world virus variant.”Clickfix“The pressure shortly rose and in the end worn out the notorious pretend browser replace scams that plagued the online final yr,” safety researcher Sheikchen stated in a report shared with Hacker Information.
“We did so by eradicating the necessity to obtain recordsdata, utilizing smarter social engineering ways and spreading by dependable infrastructure. The end result – a wave of an infection from mass drive-by assaults to hyper-targeting spearfishing lures.”
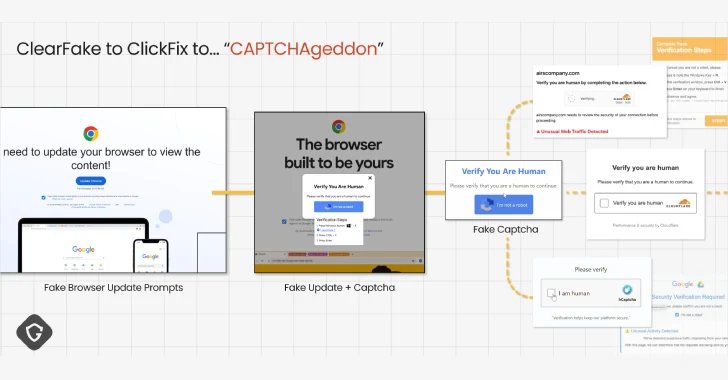
Clickfix is the title given to social engineering ways the place future targets are deceived to contaminate their machines, pose as in the event that they had been to repair non-existent points or Captcha validation. It was first detected within the wild in early 2024.
These assaults use a wide range of an infection vectors, together with phishing emails, drive-by downloads, fraud, and search engine marketing (search engine optimization) addictions, to instruct customers to pretend pages that show error messages.
These messages have one purpose. For Apple MacOS, victims will information them to comply with a collection of steps to repeat secretly copied malicious instructions to the clipboard when pasted into the Home windows Run dialog field or terminal app.

Nefarious Command triggers the execution of multi-stage sequences that result in the deployment of assorted varieties of malware, similar to steelers, distant entry trojans, and loaders, highlighting the flexibleness of the menace.
The ways have grow to be so efficient and highly effective that it results in what Guardio calls Capt Chageddon, and actors from each Cybercriminal and Nation-State have geared up them in dozens of campaigns in a brief time frame.
Clickfix is a extra stealthy mutation in Clearfake, involving leveraging compromised WordPress websites to offer pretend browser replace pop-ups that present Stealer malware. Clearfake then integrated superior evasion ways like EtherHiding and used Binance’s Sensible Chain (BSC) contract to cover the subsequent stage payload.

Guardio stated the evolution of Clickfix and its success was the results of fixed enhancements by way of propagation vectors, lures and messages diversification, and the assorted strategies used to advance the detection curve.
“The early prompts had been frequent, however they had been instantly persuasive and added clues of urgency and doubt,” Chen stated. “These tweaks elevated compliance charges by leveraging primary psychological pressures.”
A few of the notable ways in which the assault method has tailored embody the abuse of Google scripts to host pretend Captcha flows, thereby leveraging Google’s domain-related belief and embedding payloads in professional, good wanting file sources similar to socket.io.min.js.
“Obfuscation, dynamic loading, legitimately good wanting recordsdata, cross-platform dealing with, third-party payload supply, and abuse of trusted hosts like Google present how menace actors have repeatedly tailored to keep away from detection,” added Chen.
“These attackers not solely refine their fishing lures and social engineering ways, but additionally remind us that their assaults make investments closely in technical strategies to stay efficient and resilient in direction of safety measures.”